Drozer allows you to assume the role of an Android app. and interact with other apps, through Androids Inter-Process Communication mechanism (IPC), and the underlying OS.
Drozer Components
Drozer comprises three components - Agent, Console and Server.
- The Agent is an Android application that runs on your test device or emulator.
- The Console is a command-line interface that allows for interaction with the agent.
- The Server provides a central point where consoles and agents can rendezvous, and routes sessions between them.
Setup
For this tutorial we will use the Appie pentesting environment, you can read more about Appie here
This is really useful as it comes packaged with lots of tools for performing Android security testing.
The first step is to connect your device to your PC, you must ensure that USB Debugging is turned on as this facilitates a connection between the two.
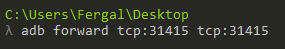
In order to get started we need to install the drozer agent on the Android device or emulator. The agent will be in the downloaded package, to install we will use ADB.
Now that the embedded server is turned on we can connect to the agent from the PC. You should see a command prompt as below.
The console allows you to run modules that are installed. In order to view the modules you can use the list command
You can also search for modules from the repository using the module search -d command, the repository is located here
Then to install - module install keyword
In the next post I will describe how to exploit vulnerable Android applications using Drozer
Download Drozer







No comments:
Post a Comment