Below is a valid XML document. To construct it we use a DOCTYPE header and gave it a name, then within that header we embed the external entity declaration. All entities begin with a declaration - <!ENTITY, we gave it the name bWAPP and also declare it as type SYSTEM - meaning local file system. This the path to the local system file that we would like to fetch our content from.
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE root [
<!ENTITY bWAPP SYSTEM "file:///[file]">
]>
For the demo we will be using bWAPP application.
First navigate to the XXE vulnerable page in bWAPP. In order to send the request to the server you will need to click on the 'Any bugs?' button.
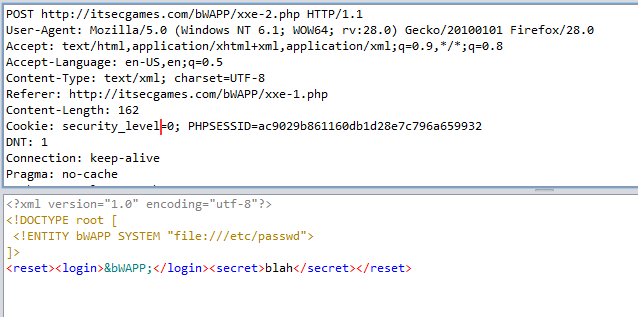
To view and manipulate the request you will need an intercepting proxy tool e.g. ZaProxy or Burp Suite. After cliking the button and checking the traffic history you will see a simple XML request with two parameters <login>bee</login> and <secret>Any bugs?</secret> .
To pull the contents back from the external entity we change the value in login parameter to &bWAPP; (note there is no validation here) the variable that stands for the system path. The XML parser should look up the value of the system entity variable bWAPP and substitute the entity declaration for the content of the file.
When we check the response we can see that the robots.txt contents are returned
We can also try to access a sensitive local resource such as /etc/passwd file. The steps will be the same as above only this time as we are calling a local file so we use file:///
Again we can see the file contents are returned in the response.
It is also possible to perform a DoS on the targets XML parser. The attack is known as the Billion Laughs attack or an XML bomb. There are 10 different XML entities lol - lol9 with the document consisting of a single instance of the largest entity, which expands to one billion copies of the first entity.
To find out more about XML and XXE attacks the following links are useful.. XML_Exteral_Entity_Attack.pdf
XML_External_Entity_(XXE)_Processing